Me and My Girlfriend:1 Vulnhub CTF Walkthrough

Normally I don’t post ctf walkthroughs simply because there are much better ones already available and I don’t see the point of adding another one. I am posting this one though because I haven’t found a walkthrough for this till now and I am hoping I am one of the first people to post a walkthrough for this CTF. This was a very easy level CTF, and I am dropping the description for this box below:
Description: This VM tells us that there are a couple of lovers namely Alice and Bob, where the couple was originally very romantic, but since Alice worked at a private company, “Ceban Corp”, something has changed from Alice’s attitude towards Bob like something is “hidden”, And Bob asks for your help to get what Alice is hiding and get full access to the company!
Difficulty Level: Beginner
Notes: there are 2 flag files
Learning: Web Application | Simple Privilege Escalation
With this note , let us start hacking!
As usual, the first thing to do is run a nmap scan for open ports:-

Port 80 looks to be the way in because anyway it was written in the description about web application. So we navigate to the ip in the browser and are greeted with this:-

My initial thought process was to try out proxies, but since this is a ctf, there might be some clues in the page source. And my hunch was right! Take a look at the clue I got:-

Hmm, so all we have to do is add that header , well we can easily do that using burp . So I fired up burp and added the header like this:-

And Voila! we got a page .Looks like the company’s page to me :-

In situations like this, I first like to try out brute force the login page or check for SQL injections which I did and I failed . I also played with the parameter for potential LFI but even that didn’t work. So with no other option, I registered myself in the register area and logged in.

I was greeted with this:-

The thing which caught my eye was the id parameter. Thinking for potential IDOR, I tried playing with it but alas I wasn’t able to change my user. No problem, let us head over to the profile part.

So it seems that the username and password is stored here. Without wasting any time I tried to change the user id . I got many other users and the creds as well which I kept noting . But I finally hit gold at user_id=5!

If you remember in the description, Alice was very important to the scenario . Now I tried logging back to the portal as alice , but I didn’t find anything. Then I remembered that we also had a ssh port open. So I tried logging in via ssh and bam! I got logged in as alice.
Creds: alice:4lic3

In priv esc, always try low hanging fruits first . Enumerating Alice’s sudo rights, I got my way in:-

Game over now, ran my php shell and opened up a netcat shell and got root!
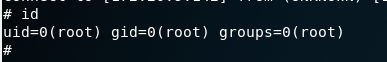
And also got the second flag(didn’t get the first one, I am assuming its somewhere in a different user)

That’ll be all for now. Thanks for reading this writeup.
P.S. I had to add the custom header manually in burp suite every time I navigated the website. On doing some research , burp seems to have an extension which can automate it , but if someone finds a way to automatically add the header, please let me know )
