Kira: CTF Vulnhub Walkthrough

Been on a vulnhub spree as of lately because of boredom I guess. This is again a very easy and simple machine . Let’s start off.
Full port nmap scan :

Seems only port 80 is open. Let’s head over there and see :

Let’s explore the uploads option. We might be able to upload a shell and get a shell. There was a simple image file upload option. We first uploaded an image to see what happens. As you can see, it even gives the location of the file:

And navigating to the location:

Alright, time to upload a shell. After some trial and error, I noticed that double extension worked well:

I set up my listener, and simply opened the file. It did not work ,it showed up this:

So there is probably a check before the file is rendered by the server. Defeated , I went back to the opening page. If you remember, there’s a language button . I navigated there and after a few clicks , I was presented this:
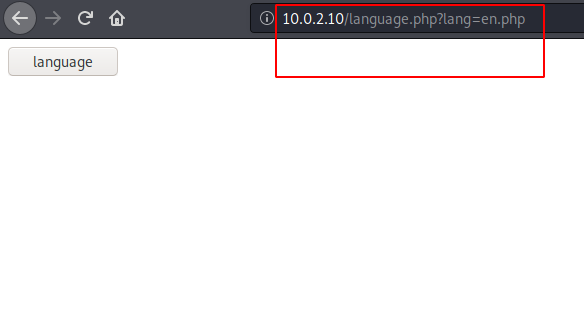
The url seems like a prime candidate for lfi . And we were right. Below is a proof of being able to read the passwd file of linux:

Then an idea struck us, why not read the shell we uploaded. We can guess the location as websites keep files in the /var/www/html location . So try that:

We get a shell!
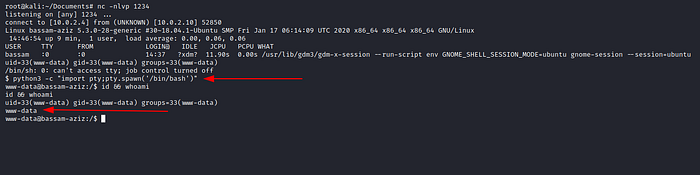
Now onto privesc, we notice a file having user creds in the website root directory:

We switched to user bassam using su:

Turns out, bassam can run find as root .

Now it’s easy, let’s become root :)

Will probably take a break from CTF’s as still have to land my first job 😜.Have a great day!
