eLection 1 Vulnhub Walkthrough:-

Hi everyone! Just solved this awesome OSCP type machine , it was really good! Now lets solve this together.
As usual we start with the full port scan . Results are as shown below

We see two ports open . Usually as we do , lets start enumerating port 80. And yes, I have changed my base to Parrot :)
Navigating to port 80, we get the default apache page

Checked for robots.txt file which had bunch of file names, out of which one worked with the directory name of election.
When we navigate to it, we see this:-

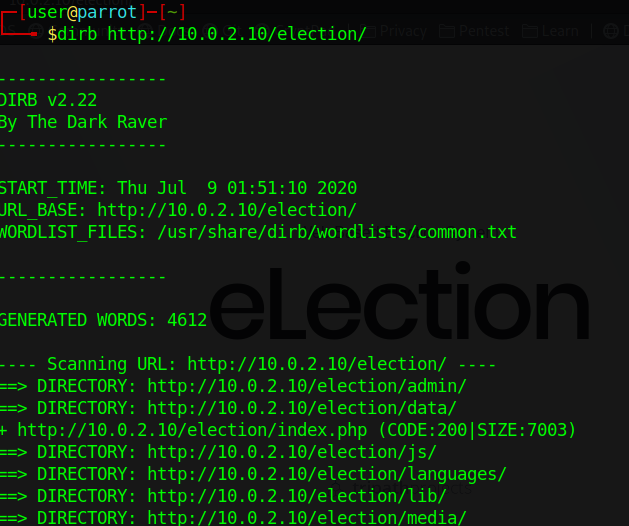
Again , nothing much for now. I tried to run a dirb and found an admin directory.
Now when we navigate to admin , we find this:-

Its asking for id. I tried a bunch of numbers , didn’t work and also it had a brute forcer in check, so clearly we shouldn’t brute force anything.
Thinking back , I ran a dirb search from the root web page as I hadn’t done that. I found a phpmyadmin login

The phpmyadmin login page:-

Tried some default creds. Got it working with root:toor :)
Now while snooping the phpmyadmin , I found this:-

These might just be what I needed for the login. I tested out the id 1234, I was right:)

Now the password in the phpmyadmin database seemed to be encrypted by md5. Long story short, tried cracking it ,couldn’t ,so I just added my own encrypted password using the word “password” .

This time I was able to login to eLection:)
Now I did a little bit of googling and landed on an exploit about the software:-
https://www.exploit-db.com/exploits/48122
I tried doing it, I was unable to .It seems the parameter was fixed even though the version was matching.
As this point I felt I might have missed something, so again reviewed my dirbscans. It turns out I did miss something , another directory:-

I quickly navigated there and found this file:-

Downloaded the file , found some creds:-

This seemed like ssh creds to me. I didn’t think it would be that simple at first. I was wrong , as it seems , they were!
Now let me quickly cat out the user.txt contents

Before running a script, I generally try to look for quick wins. So I ran a check for suids. I found an unusual one by the name Serv-U:-

Usually I’d just cat out the file or run strings to find any possible path privesc vectors. I couldn’t find anything this time. I tried googling any publicly available exploits for this and boy was I right!

It’s actually a very simple exploit, just compile the c code and run it . You wouldn’t have to change anything at all. You get a root shell if done correctly. Lets fetch the root flag .

This was actually quite a simple one to be honest. But here’s the thing, I deliberately don’t attempt the difficult ones because they usually involve a ctf element which I am never able to catch. Plus I do most of my ctf solo , so for now I am just keeping my skills sharp .
Hope you guys liked it:)
